New Feature Alert: File Retention Now Available20180123212450
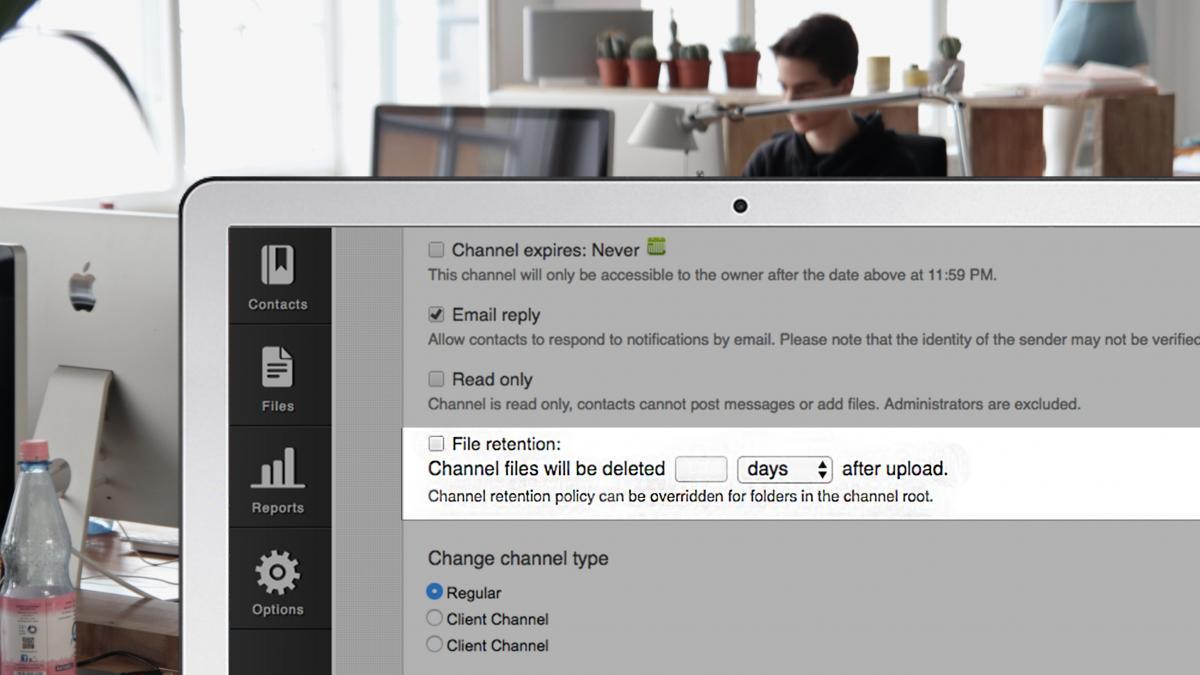
New Feature Alert: File Retention Now Available
January 23, 2018
File Retention creates new efficiencies and provides an optimal solution for compliance and security while delivering on...
The 2017 Equifax Data Breach: What’s Happened So Far20170908205509
The 2017 Equifax Data Breach: What’s Happened So Far
September 8, 2017
On Thursday, September 7, Equifax, one of the biggest credit reporting agencies in Canada and the United States, announc...
Phishing: 5 Skills We Need to Combat It in the Modern Age20170829220826
Phishing: 5 Skills We Need to Combat It in the Modern Age
August 29, 2017
A few weeks ago, our Director of Business Development received an email from our President and COO. The sender asked if ...
DLA Piper Ransomware Hack: What Can We Learn From It?20170726155647
DLA Piper Ransomware Hack: What Can We Learn From It?
July 26, 2017
The Incident On June 27, DLA Piper LLP, one of the largest law firms in the world, was hit by a ransomware attack that i...
5 Lessons Organizations Can Learn From Walmart Canada’s Data Breach20170626184328
5 Lessons Organizations Can Learn From Walmart Canada’s Data Breach
June 26, 2017
The Data Breach Word of the data breach first broke out in July of 2015, when third-party photo processing vendor, PNI D...
5 Secure File Sharing Features Your Solution Must Have20170615192508
5 Secure File Sharing Features Your Solution Must Have
June 15, 2017
Collaboration within a business is absolutely vital to the workflow of an organization. File sharing and information exc...
How to Build a Cyber Security Culture at Your Firm20170524213435
How to Build a Cyber Security Culture at Your Firm
May 24, 2017
Implementing a working culture of cyber security is difficult. Compliance is complex and rolling out a complete system a...
China Hacks U.S. Government Servers: How Government Files Can Stay Secure20150610164118
China Hacks U.S. Government Servers: How Government Files Can Stay Secure
June 10, 2015
Governments at all levels are looking to increase security measures after suspected Chinese hackers broke into the Unite...
Why Your BYOD Policy Must Include Secure File Sharing Software20150513153336
Why Your BYOD Policy Must Include Secure File Sharing Software
May 13, 2015
Does your organization have a Bring Your Own Device (BYOD) policy that prioritizes secure file sharing software? Many pe...