What are audit logs?
An audit log (also known as an audit trail) is a time-stamped record that contains a chronological list of activities that occurred in a system with the purpose of providing proof of “who did what,” and “what happened when.”
Many organizations use audit logs to detect security breaches, aid in recovery processes, and prevent unfavorable events from reoccurring.
In the case of data breaches, it’s impossible to know the extent of who or what was affected by the breach without reliable logs. Investigators would have to assume that all records were accessed and stolen when it could in fact, only be a small number of records.
It’s much easier to investigate problems in organizational security when we have access to time-stamped records of activities. Without them, we’d be taking a shot in the dark or relying on human memory and trust – which isn’t always the most reliable and will have us second-guessing what really happened most of the time.
Audit logs and compliance
In terms of compliance, many industries such as finance, accounting, legal, government, and healthcare require that sensitive information be shared in a secure fashion and are only made accessible to authorized people. Audit logging helps keep these industries compliant.
For example, in the US, the Healthcare Insurance Portability & Accountability Act (HIPAA) requires that organizations “implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.” In order to protect patient information, it’s important that only authorized people have access to those records.
Audit logs are proof to auditors that you are indeed sharing files securely and complying with privacy laws.
How does TitanFile use audit logs?
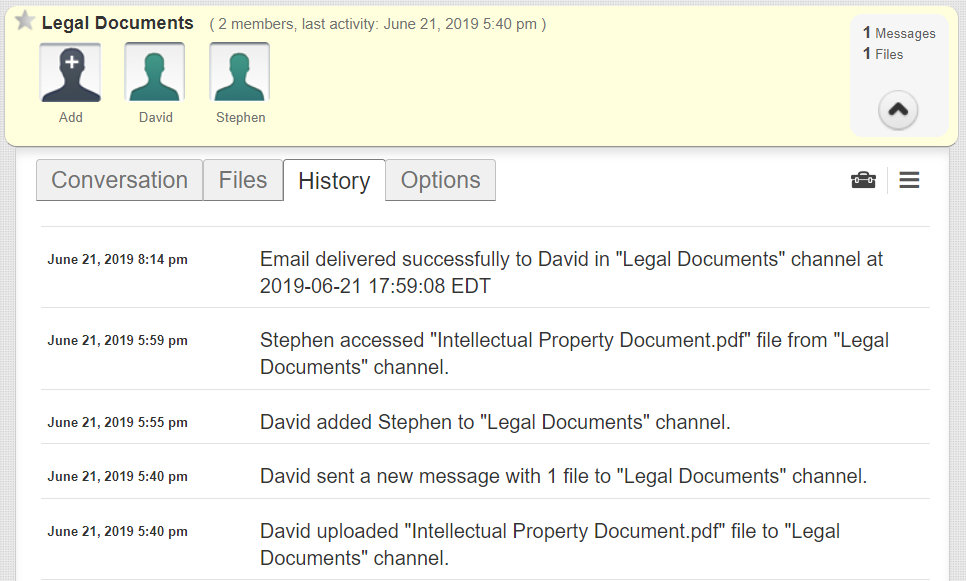
When sending messages or files through TitanFile, all user account activity is automatically recorded in audit logs and can be accessible with a few clicks. This activity includes:
- When users access their accounts
- When contacts are added to a communication channel
- When files and messages are successfully delivered to a contact’s inbox
- When files are accessed and by whom
- When settings are changed
Subscription administrators have access to the audit logs of all members under the same subscription. For your convenience, these logs can be downloaded in CSV format.
