What is Secure File Sharing?
Secure file sharing is the process of sharing files in a way that preserves the confidentiality of the data while it’s in transit from one system to another. When files are shared securely, only authorized individuals will have access to the data.
The most common way to securely share files is through encryption. When files are encrypted, only those with an encryption key are able to access the data.
Why is this important?
It’s important for businesses to share files securely because they have sensitive information they need to protect—whether it be confidential business files, intellectual property, financials, client data, or other critical information.
When data protection is not prioritized, it is more likely for an organization to experience a data breach that can lead to severe reputation and monetary consequences.
However, when files are shared securely, only the intended recipient or recipients will have access to the shared information.
Data security should be a priority at every organization.
Secure File Transfer vs. Secure File Sharing
Secure File Transfer refers to the process of sending files from one location to another over a secure connection, often using protocols like SFTP (Secure File Transfer Protocol) or FTPS (File Transfer Protocol Secure). The focus is on the safe transmission of files, ensuring data is protected in transit against unauthorized access, interception, or tampering.
Secure File Sharing, on the other hand, involves providing ongoing access to files for multiple users or teams in a secure manner. This can include access control, permissions, encryption at rest, and collaboration features. Secure file sharing platforms like TitanFile or SharePoint prioritize secure access and collaboration over time, rather than just the transmission process.
Secure File Sharing Statistics
Data Breach Costs
The average cost of a data breach in 2024 is estimated at around $4.35 million, emphasizing the importance of strong file-sharing security measures.
Adoption Rates
As of recent data, around 45% of companies have implemented secure file-sharing solutions, although many businesses still lack proper encryption for data storage or transfer.
Remote Work Security
The rise of remote work has increased data breach costs, with the average breach being $173,074 more expensive when involving a remote workforce.
Cloud Vulnerabilities
Misconfigurations in cloud environments account for nearly 23% of cloud security incidents, highlighting the need for careful management of file-sharing solutions.
Benefits of Secure File Sharing
Aside from preventing security breaches, securely sharing files has many benefits for your organization:
Protect Client Confidentiality
One of the most crucial components of corporate ethics is client confidentiality. Your clients trust you with their data and so you must do everything in your power to protect their sensitive information. Explore 6 best practices for protecting client confidentiality.
Workplace Confidentiality
Trade secrets, financial information, and company strategy are just a few of the sensitive business details that are exchanged among employees. If this information is leaked, it could give competitors insight into your business operations and impact company revenue.
By having a secure solution in place for file sharing, you can keep confidential workplace documents secure and prevent potential data theft. See more best practices for workplace confidentiality.
Remote Work
Since the onset of the COVID-19 epidemic, several businesses have implemented a hybrid work paradigm that allows employees to work both on-site and remotely from home. In some cases, employees work entirely from home. Maintaining security when employees work remotely can be challenging.
Due to the lack of in-person communication, it can be difficult to manage remote employees and monitor how they share files. By adopting a secure cloud-based file transfer solution organization-wide, you are able to standardize a secure way for employees to share confidential files.
Higher Productivity
Employees are more productive when they have access to technologies that enable them to be more efficient – a file sharing solution with automatic security is one of them.
Rather than password-protecting sensitive files, or not protecting them at all, your employees are able to easily share files securely easily over the cloud.
Control Access
Unauthorized individuals should not be able to access documents that are confidential. Today, many organizations will store sensitive data on a centralized drive, which could lead to unauthorized file access and potential leaks of data by rogue employees.
Reduced Burden on IT and Administrators
By adopting a secure file sharing platform that’s easy to use, employees are granted a self-serve solution for sharing confidential files with each other, clients, and other external parties. This alleviates the burden of secure file sharing that was original held by IT.
File Sharing Methods to Avoid for Your Business
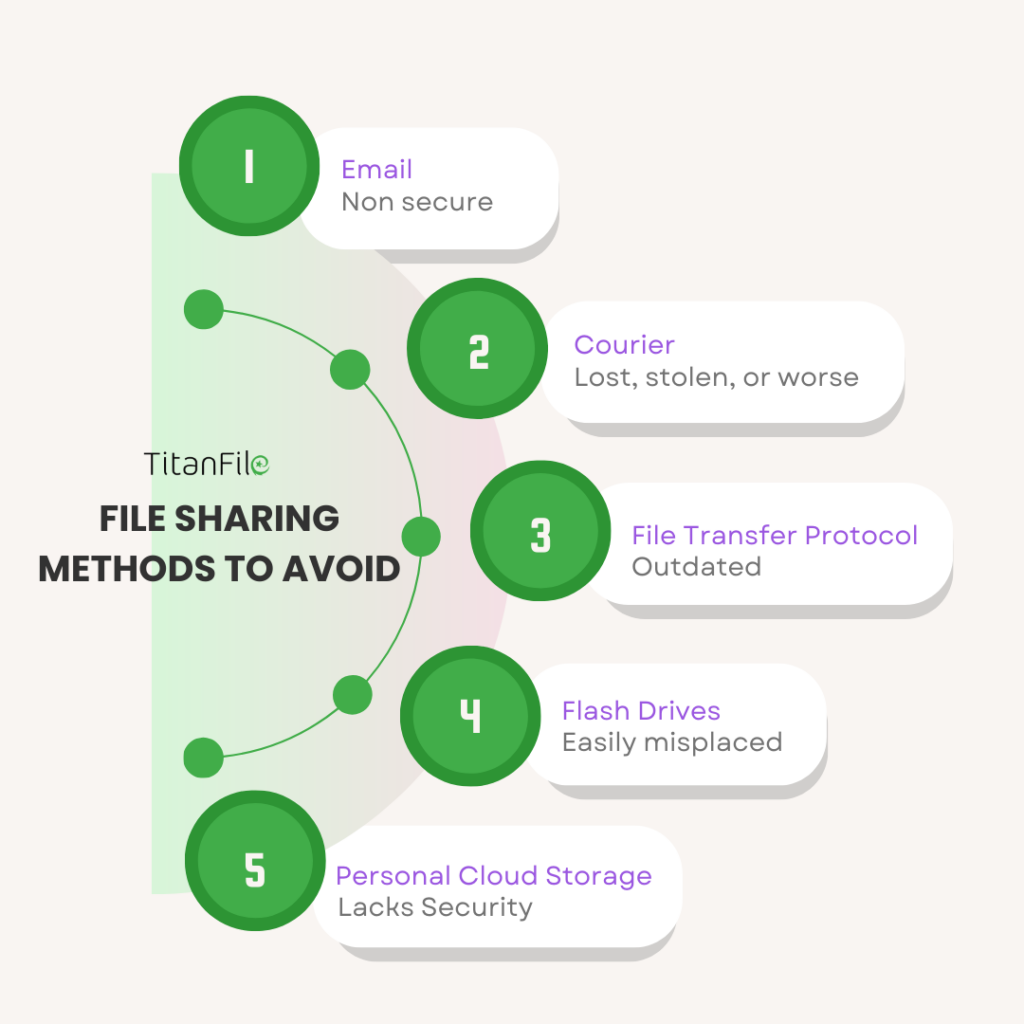
If you care about confidentiality, then there are a few file sharing services you should avoid:
Email is great for general correspondence but when it comes to sharing sensitive information, email should be avoided at all costs. Outgoing emails are typically not encrypted, thus there is the chance that the data will be intercepted by hackers and misused without your permission.
Learn why email is not a good solution for secure file transfer.
Courier
It’s not uncommon for packages to get lost in the mail or delivered to the wrong address by mistake. If the package carrying your information gets lost, your private documents could end up in the wrong hands.
File Transfer Protocol (FTP)
FTP does a good job of facilitating transfer from one system to another, however, it was not originally designed to be secure. Experienced hackers can easily brute force a user’s credentials and intercept the information being transmitted.
Flash drives / external hard drives / DVDs
Physical storage devices such as flash drives, hard drives, and DVDs are physically small devices that are easy to misplace. Misplacing one of these units with confidential information on it can lead to unauthorized access to that information.
Personal cloud storage accounts
Personal storage accounts lack the security and compliance requirements that are necessary when sharing confidential information in highly-regulated industries. Since these are often non-corporate accounts, they are often not regulated by your workplace and do not have audit trails.
P2P
P2P networks often lack encryption, making data vulnerable to interception. They are also frequent targets for malware, increasing the risk of downloading infected files. P2P systems provide limited access control, so once a file is shared, it’s difficult to manage who can access or modify it, potentially leading to data leaks. Additionally, P2P networks expose user IP addresses, and there is no audit trail to track file activity, which complicates compliance with regulations. These issues, combined with potential legal risks, make P2P unsuitable for secure file sharing.
Industries That Need Secure File Transfer
Any organization that sends or receives confidential information is in need of a secure way to share files. Some of the most highly-regulated industries include:
Accounting & Financial Services
Financial service providers and accountants understand the value of privacy. Financial information on a company reveals both its strengths and weaknesses. Such information must be discreetly analyzed and interpreted until it is prepared for dissemination to stakeholders. Secure file sharing is essential to the success of finance-related companies as they collaborate with other businesses.
Healthcare
Healthcare providers have access to a lot of confidential patient information referred to as Protected Health Information (PHI) or Personally Health Information. Under regulations, such as HIPAA and PIPEDA, this information needs to be kept secure at all times- whether it’s in transit or at rest.
Government
Important documents are continually shared between regulatory agencies and governments. Although timely collaboration is critical in this industry, it’s equally important to maintain the confidentiality of the documents shared.
Legal
Legal professionals recognize the significance of maintaining client confidentiality. Protecting the confidentiality of client documents is necessary to uphold their best interests. Throughout the many practice areas of law firms and their use cases including litigation, discovery, production, and corporate transactions, an efficient, yet secure file-sharing solution is essential to the firms’ success.
Common Use Cases For a Secure File Sharing Platform
A secure file-sharing solution can help address several use cases in your organization including:
Data Security
Managing confidential and sensitive company and customer information requires top-tier data security. There are thousands of cyberattacks per day which can result in data breaches and stolen information. Security has now become a top priority for firms that manage client documentation.
With a configuraable secure file sharing solution like TitanFile, even the most complex information security management systems (ISMS) can be configured to keep company data secure. Administrators can have complete control over data via granular access controls, audit trails, and user delegation features.
Large File Transfers
One of the most important and prominent use cases for need a secure file transfer solution is the ability to send and receive large files. When there’s a file size limit, it’s difficult to remain productive.
A good file transfer solution will make it simple to files of all sizes, types, and volumes over an encrypted network without the inconvenience of transferring files via FTP or mailing packages of paperwork and flash drives.
Compliance With Industry Standards
If you manage confidential client information, chances are, you need to abide by compliance standards to protect them.
Depending on the jurisdiction and industry your business resides in, you are required to follow specific standards; for example, GDPR in Europe, PIPEDA in Canada, and HIPAA in the U.S. Failure to comply with these standards may result in fines up to $1,000,000 and most importantly, the loss of client trust.
It can be difficult to ensure that all requirements are met without the assistance of a third-party. Fortunately, when it comes to file sharing, there are many many secure file sharing companies today that have dedicated compliance teams to ensure that their platforms are compliant with industry standards and regulations.
Learn more about compliance:
Workplace Confidentiality
Workplace confidentiality is a set of policies and procedures created to protect the integrity of sensitive or potentially damaging information handled in the workplace.
Workplace confidentiality dictates information handling practices and maintains the privacy of confidential information. It is easily maintained through the use of secure file transfer solutions which meet compliance requirements and protect information from unauthorized users.
Secure Client Portal
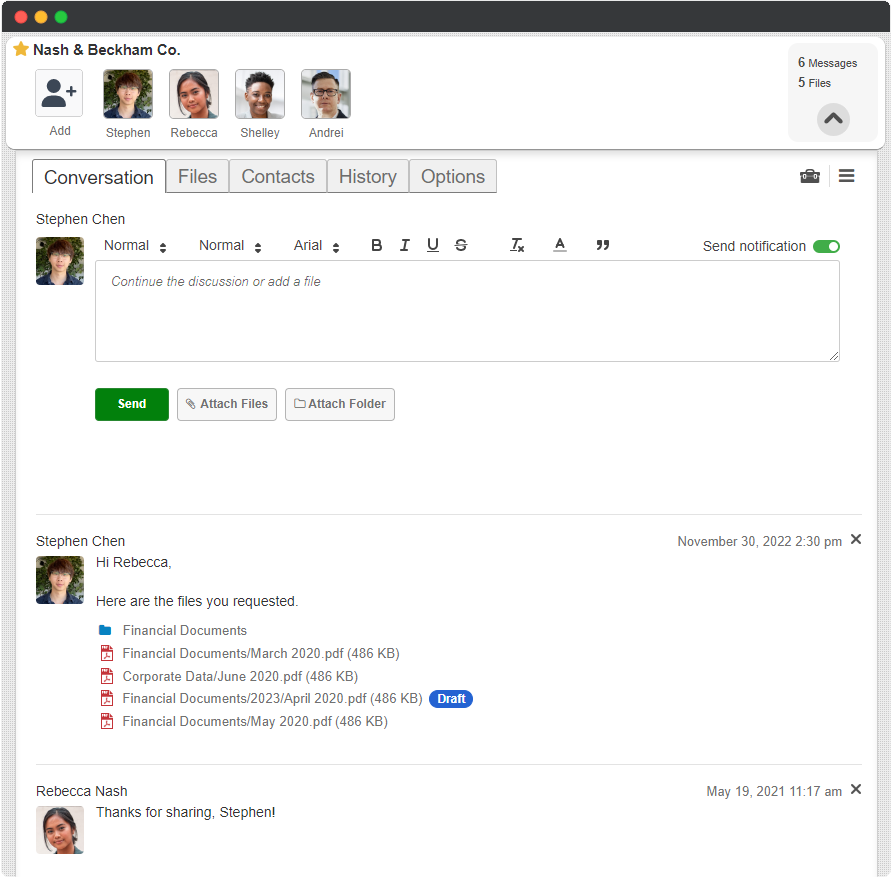
Secure client collaboration plays an important role in highly-regulated industries. The ability to effortlessly communicate with clients results in improved productivity, clarity, and overall satisfaction for all parties involved.
Secure file sharing platforms can act as a secure client portal that you can use to exchange confidential information with your clients in a single, centralized location. Staff and clients will have peace of mind knowing that their private information is kept secure at all times.
Ad-Hoc File Transfers
The term “ad hoc” means “person to person.” In terms of file sharing, ad hoc file transfer represents scenarios where you need to quickly share files with someone without having to go through the hassle of setting up a user account for the recipient. You should be able to quickly add a file, add a recipient, and click send.
Whether you’re sharing files among your colleagues, with clients, or with outside parties, a secure file-sharing solution will enable you to efficiently share sensitive data.
Secure File Sharing for Business Types
Secure file sharing is crucial for businesses of all sizes, but its importance and implementation can vary based on the business type, whether it’s a solo professional, a small business, or an enterprise.
Solo Professionals
For solo professionals, secure file sharing is vital for protecting client data and maintaining trust. Whether a lawyer, consultant, or freelancer, they often deal with sensitive information that requires confidentiality. Using secure platforms helps meet compliance standards, avoid data breaches, and ensures they can securely collaborate with clients.
Small Businesses
For small businesses, secure file sharing becomes even more critical as they grow and start managing internal teams alongside external clients. Small businesses often handle confidential client files, financial data, and intellectual property. Secure file sharing platforms allow them to set access controls, track file activity, and maintain security without investing heavily in IT infrastructure. It also helps small teams collaborate more efficiently while meeting legal and regulatory requirements.
Enterprises
For enterprises, the stakes are even higher due to the scale of data handled, the number of employees, and regulatory pressures. Enterprises require robust secure file sharing systems that integrate with existing infrastructure, offer advanced features like encryption, user permissions, data loss prevention, and detailed audit trails. These systems ensure compliance with industry-specific regulations like GDPR, HIPAA, or CCPA, protect against cyber threats, and facilitate seamless collaboration across departments and global offices.
How to Transfer Files Securely
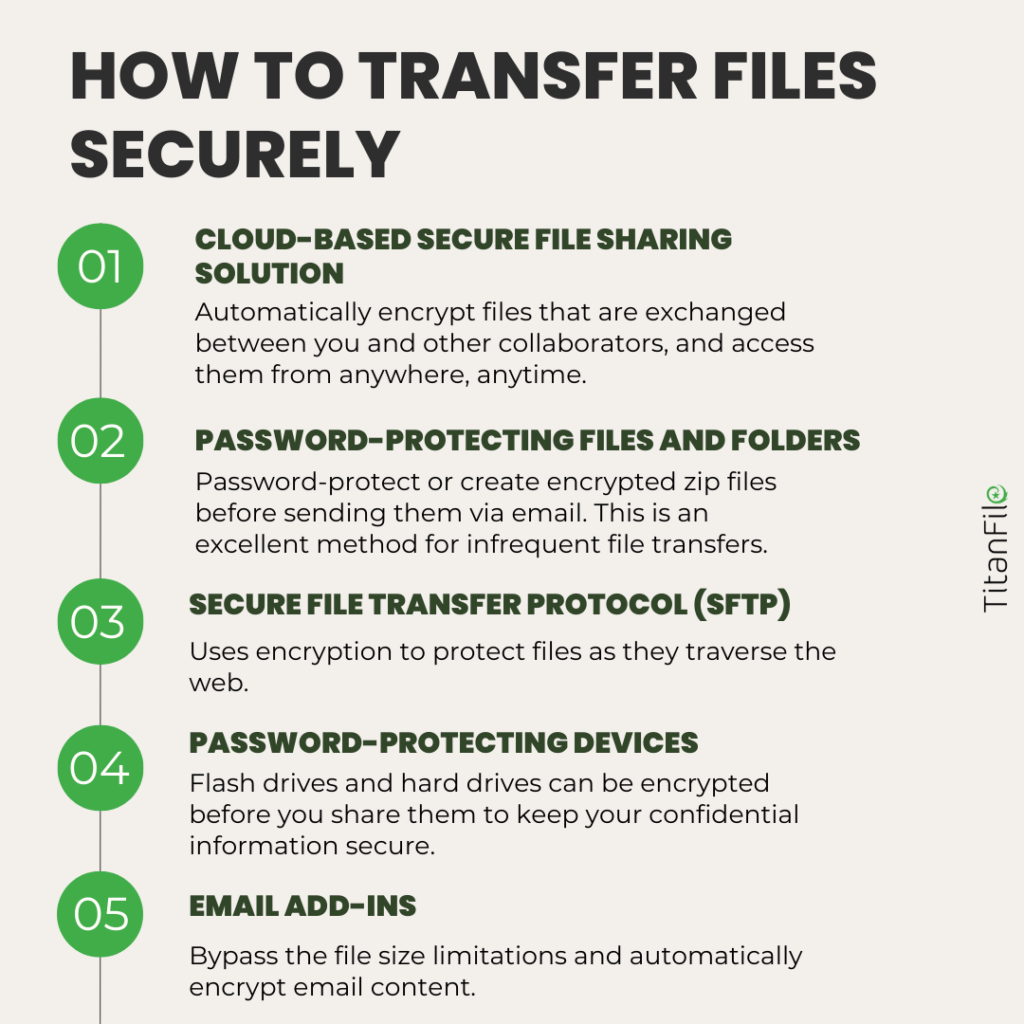
If you’re looking to adopt a secure file sharing service, there are several options you can choose from. Below, we’ve listed the most modern file sharing services today.
1. Cloud-based Secure File Sharing Solution
Cloud-based secure file-sharing solutions have become the standard for transferring files. They enables you to automatically encrypt sensitive data that is exchanged between you and other collaborators.
These platforms are typically web apps that utilize cloud storage, which means they are accessible from anywhere on a desktop computer or mobile device, giving your employees the flexibility they need to exchange confidential files from the office or remotely.
Some cloud-based file sharing platforms also integrate with platforms such as Outlook, Docusign, document management systems, and other collaboration software.
2. Password-Protecting Files and Folders
Password protection is among one of the most common secure ways of sharing information. For files smaller than 20MB, you can password-protect them or create encrypted zip files before you upload files and send them as email attachments. This is an excellent method for infrequent file transfers.
When relying on this method, it’s important to use strong passwords.
If you’re working with larger files or a high volume of information, this method is may be insufficient.
3. Secure File Transfer Protocol (SFTP)
Secure File Transfer Protocol (SFTP) offers the same functionality as traditional File Transfer Protocol (FTP) except it introduces a security component. SFTP uses encryption to protect files as they traverse the web. SFTP uses SSH and encrypted File Transfer Protocol (FTP) commands to prevent password theft and protect sensitive information.
It’s good to note that the process behind SFTP can be quite time-consuming and inefficient. Not only do transfers take longer to set up, but often IT intervention is required since the average employee does not know how to use SFTP.
4. Password-Protected Devices
Flash drives and hard drives can be encrypted before you share them to keep your confidential information secure. When these devices are encrypted, even if they were lost in transit or delivered to the wrong address, unauthorized parties would not be able to access the contents without the password or encryption keys. However, it can get quite expensive to purchase these types of hardware and ship them out on a regular basis.
5. Outlook Integration
It’s common practice to send documents via email but is it safe? 94% of malware is delivered by email which makes the confidential information you share susceptible to breaches. Additionally, email is not automatically encrypted – if an unauthorized agent accesses your account, the information is easily readable.
In order to share sensitive documents securely through Outlook, you can use an add-on such as TitanFile’s Secure Send Outlook Integration. With this tool, users can bypass the file size limitations that email imposes on documents bigger than 20 MB. As well, all email content is automatically encrypted in transit, end-to-end, and at rest to protect your information through every step of the file-sharing journey. The best part? You won’t have to leave Outlook to send files securely.
What Are the Challenges of Securely Sharing Files?
Securely sharing files comes with several challenges, particularly as businesses strive to protect sensitive data and ensure compliance with regulations. Key challenges include:
Data Security
Ensuring files are encrypted both in transit and at rest is crucial. Unencrypted files can be intercepted or accessed by unauthorized parties, leading to data breaches or leaks.
Access Control
Managing who can access files, how they access them, and what actions they can take (view, edit, download) is a complex task. Without proper controls, files can be shared with unintended recipients, exposing sensitive data.
User Error
Human error, such as sending files to the wrong email address or mishandling permissions, can undermine even the most secure systems. Inadequate user training and lack of awareness increase these risks.
Compliance and Legal Requirements
Different industries must comply with various regulations (e.g., HIPAA, GDPR, CCPA), which often dictate how files should be shared and stored. Meeting these requirements can be difficult, especially for businesses without dedicated IT resources.
Scalability
As organizations grow, they handle more data and involve more users in file sharing. Maintaining security across a large, dynamic network with multiple points of access can strain systems and policies, increasing the risk of security breaches.
Integration with Existing Systems
Many organizations use a mix of tools for communication, storage, and collaboration. Ensuring a secure file sharing platform integrates seamlessly with these tools while maintaining security protocols can be challenging.
Remote and Mobile Access
With the rise of remote work and mobile device usage, ensuring secure file sharing across various devices and locations becomes more difficult. Security measures must extend beyond the office environment, protecting data from external threats like unsecured networks or lost devices.
File Size and Transfer Speed
Large files can be difficult to share securely due to size limitations or slower transfer speeds. Finding secure solutions that handle large file sizes without compromising on speed or security can be a challenge for organizations.
How to Choose Secure File Sharing Software
If you’ve come to the conclusion that you need to adopt a new secure file transfer solution, the first step you should take is to create a list of the requirements the solution must adhere to.
Not sure where to start? Here are some must-have features and capabilities to add to your secure file transfer checklist:
Secure File Transfer Platform Checklist
- State-of-the-Art Security
- Two-way File Sharing
- Audit Trail
- Large File Transfer
- Employee and Client Satisfaction
- Fast Upload Speeds
- Support for Company Uses Cases
- Reliability
- Access Controls
- Compliance
- Accessibility
- Outlook Integration
- DocuSign Integration
- Document Management System Integration
- Configurable security controls and security features
- Configurable Expiration Date for Files
- Two-Factor Authentication
- Compatibility With Mobile Devices
Start a Pilot Program
Once you’ve narrowed down some candidates, you want to ensure that they meet your expectations.
Many file sharing providers allow you to trial their software or undergo a Proof of Concept (POC) process to see if the platform is the right fit for you and your colleagues. Take advantage of these trials and give access to employees that would typically need to share confidential files on a regular basis.
If employees respond well to the solution during the pilot, you may have a winner!
How to Onboard Your Business to a Secure File Sharing Platform
Implementing a secure file sharing platform is a critical step in protecting sensitive data and streamlining collaboration. Here’s how to get your business onboarded successfully:
Before Onboarding
Start by evaluating your business’s specific security needs. Understand the types of files you’ll be sharing and the compliance requirements you need to meet (e.g., HIPAA, GDPR). Choose a secure file sharing platform that aligns with these needs and audit your current workflows to identify gaps that the new system will address. Have a clear strategy for data migration if you’re moving from another system.
Onboarding the Team – Checklist:
- Set up user accounts and assign roles.
- Define user permissions and access levels based on roles.
- Conduct training sessions to ensure your team understands how to use the platform securely and effectively.
- Test the sharing and collaboration features to ensure smooth workflow integration.
- Create a plan for handling support requests and troubleshooting during the initial phases.
Timelines
Plan for a phased rollout. Initial setup, including user account creation and system configuration, should take around 1 week. Allow an additional 1-2 weeks for team training and troubleshooting. By the end of 2-3 weeks, your team should be fully onboarded and using the platform confidently.
Maintenance Tips
After onboarding, perform regular security audits to ensure that permissions are up-to-date. Monitor user activity to spot any irregularities. Stay informed on platform updates and features to keep your system secure and efficient. Regularly remind your team of best practices for secure file sharing.
With proper planning and a clear process, you can quickly onboard your business to a secure file sharing platform while ensuring data protection and enhancing collaboration.
Why use TitanFile to Share Files?
TitanFile is an award-winning secure file-sharing platform that is consistently rated as the most secure file-sharing solution among several third-party rating sites such as the SecurityScorecard.
Among other file sharing services, TitanFile stands out as the most intuitive platform for even the most non-technical employees and clients, enabling them to have self-serve access to send and receive files on their own without sacrificing security.
Furthermore, TitanFile is compliant with industry standards such as ISO 27001, SOC 2 Type II, HIPAA, PIPEDA, GDPR, and PCI DSS, offering advanced security features and giving your employees and external collaborators peace of mind.
